Author: Kumaragunta Harisaiprasad, CISA, APP, ISO 22301 LI, ISO 27001 LA, ISO 9001 LA, Six Sigma Green Belt
Date Published: 16 September 2020
Related: Risk IT Framework, 2nd Edition | Print | English
Enterprise Security Risk Management (ESRM) is a holistic security program designed to identify and prioritize assets and risk to mitigate those risk areas. ESRM bridges security professionals and asset owners in making informed decisions through the ESRM cycle.
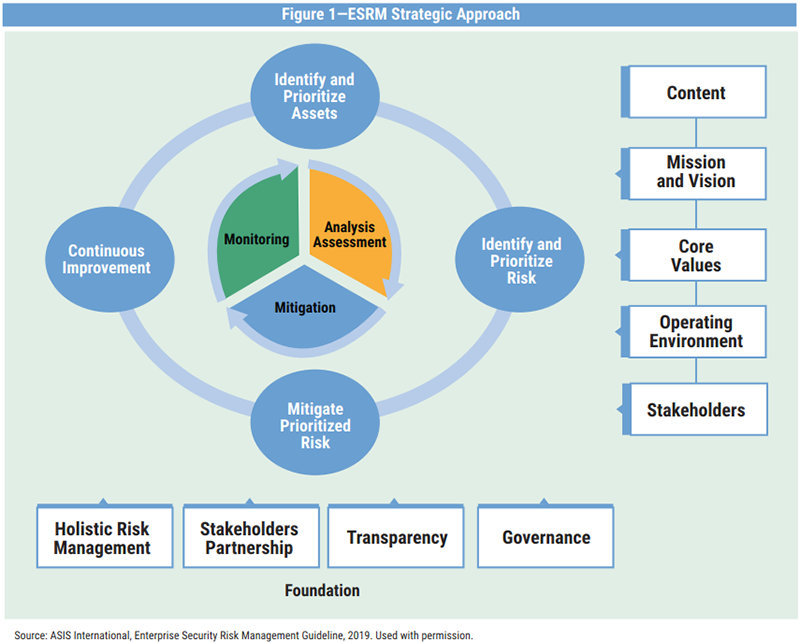
The ESRM cycle shown in figure 1 is based on new ESRM guidelines from ASIS, 1 which were drafted based on globally established and accepted risk management principles, implemented by identifying, evaluating and mitigating the security risk areas of an enterprise to reach its business objectives. Practicing ESRM helps an enterprise improve the maturity of its security process. This cycle can be initiated after understanding an enterprise’s context. Understanding the context involves understanding the mission, vision, core values, operating environment (i.e., physical, nonphysical and logical) and stakeholders. This helps security professionals identify the risk areas that restrict the organization in achieving its goals and objectives. The ESRM cycle includes four processes:

Emerging risk can be determined through investigation and analysis. In this process, root causes are identified, mitigation controls are devised and prioritized and response time is monitored.
Sharing of security information with asset owners and stakeholders forms an important part of the continuous improvement process. This helps security professions send and receive information from asset owners, which contributes to continuous improvement.
ESRM addresses mitigating risk from physical security, cybersecurity, information security, loss prevention, organizational resilience, brand protection, travel risk, supply chain security, business continuity, crisis management, threat management, fraud risk management and workplace violence prevention. Its approach is shown in figure 1.
The ESRM program for an organization can be started with an assessment using the ASIS ESRM maturity assessment tool, 2 where the rating for various categories is based on the current people, process and governance scores. The current people and process scores are shown in figure 2.
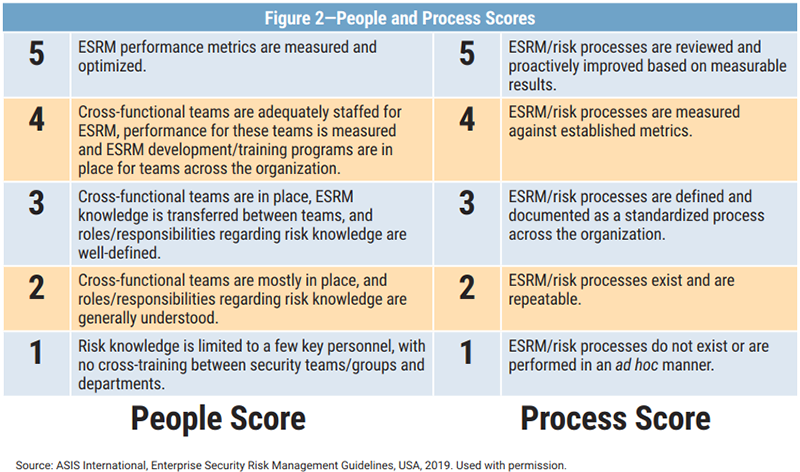
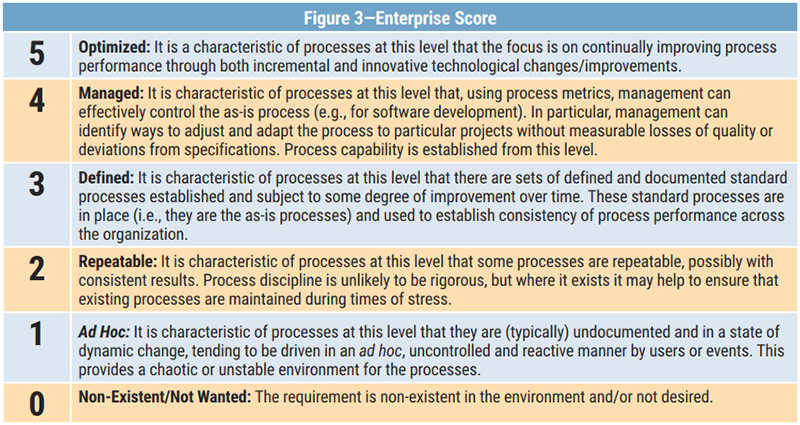
A governance score consists of a risk rating and thresholds set by the enterprise risk governance committee. The assessment tool consists of different categories that include program strategy, program governance, understanding and awareness, program implementation and application, program management and advancement, and alignment of security risk mitigation activity. Each category has different controls and, for each control, a people score, process score and governance score between one and five should be given to get the enterprise score. The values and definitions of an enterprise score are shown in figure 3. An average score for each of the six categories is given for people, processes and governance, respectively, by the online tool. The current level score and the recommended level is also provided by the tool for each of the six categories. Areas covered under each of the six categories include:
Periodic reviews and audits help assess the status of ESRM and continuous improvement. Communications with external and internal stakeholders on the performance of risk management make the governance process of an enterprise effective.
ISO 27005 is a standard for information security risk management, which describes how risk should be assessed and managed and provides a risk matrix to determine risk levels of various risk areas. ISO 31000 and the Committee of Sponsoring Organizations of the Treadway Commission (COSO) only discuss risk management and principles for an enterprise. 3 ESRM specifically addresses managing security risk areas of an enterprise, and this framework is designed in such a way that it can integrate well with the enterprise risk management framework. This is because an enterprise score from the ESRM maturity assessment tool uses defined people and process scores and leaves the governance score to be defined by the particular enterprise. None of the other standards have a provision to determine the risk management rating at an enterprise level. This helps an enterprise assess the maturity level of security risk management and determine the road ahead through the ESRM tool.
The results of a simulated enterprise that has used the ESRM tool and completed the survey is shown in figure 4.
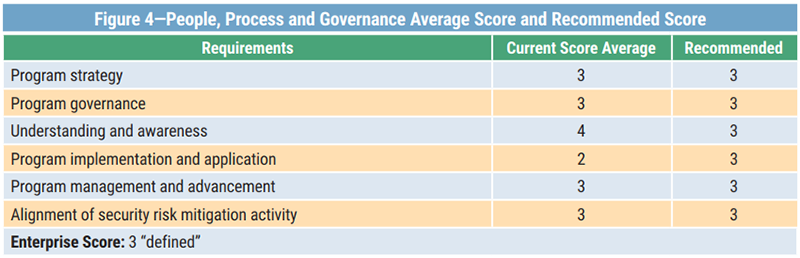
The enterprise score is calculated and the current average score of each category determined. In this example, even though the enterprise score is in the desired level, the enterprise did not achieve the recommended score in the program implementation and application category and achieved an above-recommended score in understanding and awareness (figure 4). The ESRM survey not only calculates the overall enterprise score, but it also informs which area an enterprise needs to improve and what level the enterprise has achieved in each category. From this, an enterprise can revise and implement strategies to improve its ESRM and achieve required scores of performance.
1 Professional Standards Board; “Guideline: Enterprise Security Risk Management,” ASIS International, September 2019
2 ASIS International; “ESRM Maturity Assessment Survey,” https://www.asisonline.org/publications-resources/esrm/esrm-survey/
3 International Organization for Standardization, ISO 31000:2018 Risk Management—Guideline, Switzerland, February 2018, https://www.iso.org/standard/65694.html
Is an associate consultant with Mahindra Special Services Group with more than 12 years of experience in the industry. He is the ISACA ® New Delhi (India) Chapter leader and social media chair. He is also a topic leader for the ISACA Certified Information Systems Auditor ® (CISA ® ) online forum. He is a frequent contributor to blogs and has published articles related to the information security domain in ISACA Now, COBIT Focus and the ISACA ® Journal. He conducts user awareness training, internal auditor training, International Organization for Standardization ISO 27001 audits, regulatory audits, third-party audits, internal audits, IT audits, risk assessments and implements ISO 27001, among other tasks. He can be contacted at harisaiprasad@gmail.com.